In recent years, the banking, financial services, and fintech industries have become aware of the security risks posed by social engineering.
However, fraudsters don’t concern themselves with regulations, customers, or ethics. They are free to act quickly and opportunistically, with the latest technology and tools available, and without needing to stick to plans or roadmaps. They are always evolving more quickly than security systems. And a big current threat that is less discussed than social engineering is the vulnerability of your customers’ mobile devices — particularly, their phones.
Why your customer’s phone is a potential attack vector
Fraudsters can gain access to a phone’s data and clone it in a number of ways. For example, they can use a SIM scanner, which is a small device that enables them to scan a phone from a short distance, or an app that they download onto their own phone. These enable the fraudster to obtain key information from the phone and replicate the digital identity of the phone’s owner.
Or they can adopt a SIM swapping approach, like the one used to take over Jack Dorsey’s account. This enables the fraudster to intercept any one-time passwords sent via text allowing them to circumvent many two-factor authentication methods, including their bank accounts. Biometrics hacking can also help criminals bypass phone authentication applications. This can be achieved by accessing biometric data on the dark web, or taking a picture of a person’s iris or finger, and making a mold of their finger.
There are always low-tech approaches too. A fraudster can simply observe someone entering their PIN and steal the entire phone, not for the physical phone itself, but in order to access financial data and banking apps.
These kinds of attacks can happen virtually anywhere. However, to do as much damage as possible, fraudsters need time to infiltrate their victims’ accounts. Therefore, attacks are more common at places such as airports or festivals, where people tend to be distracted for extended periods of time, and less likely to use their phone or check their bank account. In these situations, a person may go for many hours or more than a day before they realize that their bank balance has been reduced. And even if they do realize their phone is missing, they may assume that authentication features already in place, including PIN and facial recognition, will ensure that their sensitive data is inaccessible.
The challenge of ambiguous-looking fraud
These kinds of phone-based fraudulent attacks — where apparently genuine credentials are used to access financial data — present a big challenge to customers and financial institutions alike.
Consider this example. In London in early 2023, a pickpocket stole a mobile phone. While upset by the theft, the victim initially didn't think much more of it until the morning after when he checked his online banking, only to find that the thief had somehow used his banking apps to steal over £20,000. His bank, Barclays, did an internal fraud investigation which later resulted in the victim being held liable for all the losses, since it looked like the PIN had been entered to access the funds.
This is one example of a common issue. If a transaction is made from an account where all the login information, metadata, and sometimes even biometric data seems to belong to the account holder, then who is to say that it actually is fraudulent?
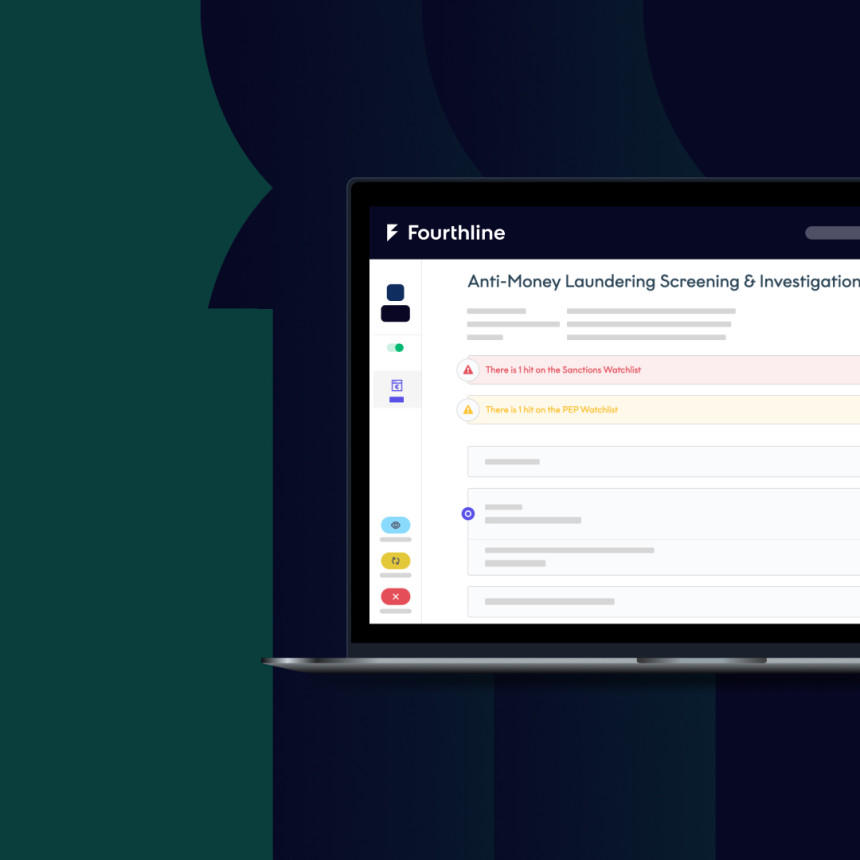
Introducing Fourthline account authentication — a light-touch way to verify identity
When tackling this kind of ambiguous-looking fraud, the temptation is to look for the usual signifiers of potential fraud such as large withdrawals, unexpected locations, and other suspicious activity, and put a temporary block on the card.
But this is a sub-optimal approach. For example, if it is actually a genuine transaction, this frustrates, annoys, and even embarrasses your customer. If done often enough you could lose them altogether, risking a loss of revenue. On the other hand, you don’t want to approve large suspicious-looking transactions for all kinds of financial and reputational reasons.
To protect your customer, your reputation, and your revenue, you need a non-intrusive, accurate, and speedy way to ensure that the person performing a suspicious transaction is the person who owns the account. That is where a solution such as Fourthline account authentication can help.
In brief, here’s how it works:
Your rules for suspicious activity (large amount, different device, unusual location, and so on) alert Fourthline via an API call.
The customer is asked to verify their identity via a biometric check, where they look at the phone’s camera and turn their head from side to side. Meanwhile, Fourthline also checks a range of phone metadata, including language settings, which have a high correlation with fraudulent activity. And it is also important to note that Fourthline’s proprietary technology is able to stop all kinds of biometric fraud, including stolen or AI-generated photos or videos, silicon masks, and more.
If the person is the account holder, the transaction can continue, and if not, the transaction is paused.
Fourthline account authentication is so effective that with some organizations which didn’t use its onboarding KYC, it has captured more fraud than the initial onboarding KYC process. Furthermore, we can help manage account security and share fraud trend analysis with partners.
Now let’s go back to our example from London above. In this unfortunate situation, the victim was on the hook for his losses as the bank claimed that the withdrawal had been legitimate. But with a solution such as Fourthline account authentication, this kind of suspected fraud, in which large amounts of money are withdrawn in a suspiciously short period of time, could be stopped with a simple, light-touch authentication step. Instead, as it stands, the customer is out of pocket by a large sum of money, the bank suffers from reputational damage, and this issue causes unnecessary expense and time investment for everyone involved.
Stop fraudsters, not customers
Social engineering remains an ongoing threat to consumers’ financial data. But fraud evolves quickly. And fast, non-intrusive verification checks such as those offered by Fourthline account authentication have a range of benefits. They help build trust, as your customer will appreciate that a check is performed, but not at the expense of the customer experience. They reduce fraud, but not at the expense of stopping genuine transactions that look like fraud. And at scale, they have a positive impact on revenue.
To find out more about Fourthline account authentication, contact us.